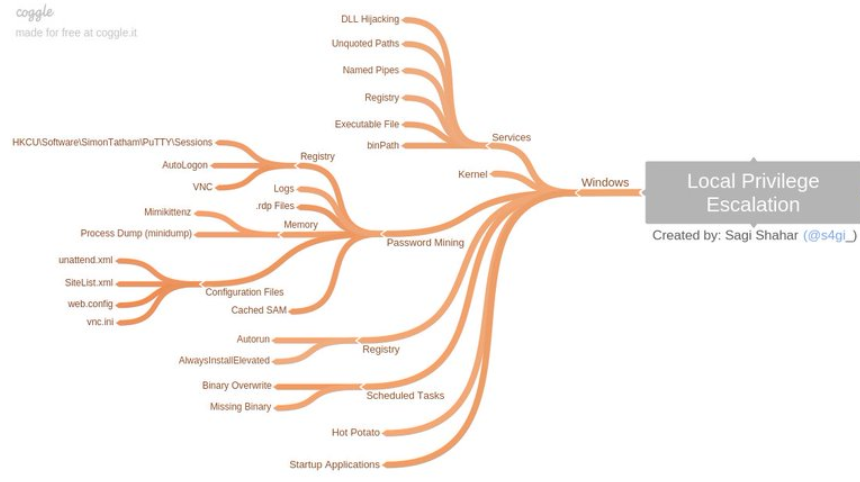
Offensive Security Tool: PEASS (Privilege Escalation Awesome Scripts Suite) As Shell is the beginning, once a hacker accesses a system, which is not so... | By Black Hat Ethical HackingFacebook

What Is A Privilege Escalation Attack? How To Prevent Privilege Escalation Attacks? - The Sec Master

NoFilter: Tool that Escalates Privilege Abusing Windows Filtering Platform - GBHackers on Security | #1 Globally Trusted Cyber Security News Platform

Linux Exploit Suggester - Linux Privilege Escalation Auditing Tool - Kali Linux 2018.1 – PentestTools
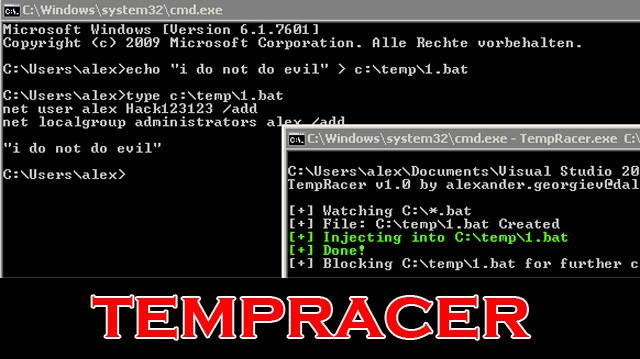
TempRacer - Windows Privilege Escalation Tool - Darknet - Hacking Tools, Hacker News & Cyber Security
![Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube](https://i.ytimg.com/vi/p-MoSi5WvIM/maxresdefault.jpg)
Linux Privilege Escalation - Automated Tools [HINDI] | Part_02 | PentestHint | LinPeas Tutorial - YouTube

TryHackMe — Jr Penetration Tester | Privilege Escalation | Linux Privesc | Part 2 | by Aditya Sharma | Medium